News
22 hours ago by Robert Keim
Maxim Integrated has cracked to more secure authentification—without a digital key stored in the IC’s memory.
Security is a major issue these days, and engineers must be increasingly cognizant of the ways in which their devices might be vulnerable to data theft, reverse engineering, or cyberattacks that allow a hacker to disable or gain control of an embedded device.
I tend to think of security from the perspective of either remote interference carried out through a network connection or the mischief that people can cause when they have direct physical access to a device. However, there is another aspect of electronic security that is important in a wide variety of applications, namely, authentication.
An authentication scenario involves a host device and a connected device such as a peripheral or a subsystem. The fundamental issue here is whether the connected device is authentic. The host wants to be sure that the connected device is produced by an accepted manufacturer, or that it will function properly and safely, or that it won’t steal sensitive data.
In this article, we’ll discuss authentication and Maxim’s interesting security technology integrated into the newly-released DS28C39.
What Is an Authenticator IC?
An authenticator IC includes security and communication features that enable the host to interrogate the connected device and confirm that it is authentic.
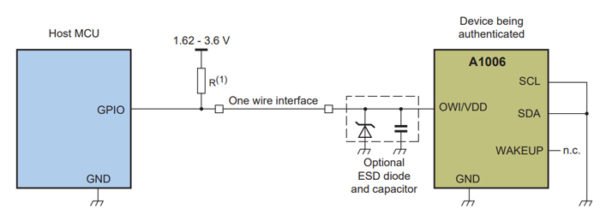
The following diagram conveys the general idea of authenticator implementation. A microcontroller in the host device communicates with the authenticator IC, which is incorporated into the design of the connected device.

The A1006 supports communication via the 1-wire interface or I2C, whereas the DS28C39 uses only I2C. Image used courtesy of Maxim Integrated
Authenticator Applications
I suspect that many electrical engineers have spent little if any time thinking about authenticators.
Nevertheless, the list of possible applications is quite long and spans multiple industries: Medical systems may need to authenticate peripheral devices. An IoT node that is added to a network might require authentication. Consumer devices can use authentication for brand integrity or detection of clones. Software access can be restricted or managed by means of authentication devices.
One interesting thing that I noticed is that authenticator ICs don’t seem to be intended specifically for military applications, but surely the military needs just about every type of security technology imaginable. If you have any experience with authentication in the defense industry, maybe you could share what you’ve learned in the comments section.
ChipDNA Secure Authentication
The DS28C39 is a six-pin, 3 mm × 3 mm, 3.3 V device that operates from –40°C to +85°C and supports I2C communication at serial-clock frequencies up to 200 kHz. It offers an impressive array of security features, including cryptographic protection of all stored data, true random-number generation (TRNG), and data read/write authenticated via the elliptic curve digital signature algorithm (ECDSA).
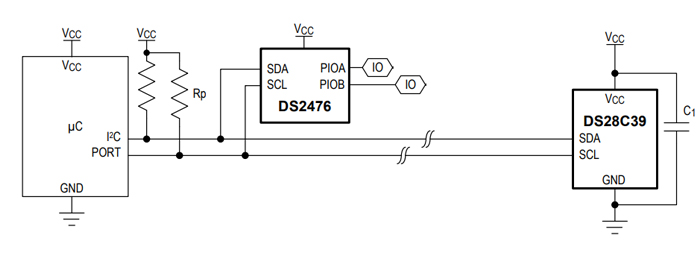
The DS2476 is an embedded-security coprocessor. This is the typical application circuit. Image used courtesy of Maxim Integrated
“ChipDNA” is Maxim’s name for a technique that they use to make security ICs extremely resistant to attacks that attempt to compromise a system by obtaining a cryptographic key. In fact, Maxim describes ChipDNA as “immune to all known invasive attack tools and capabilities.”
What makes this technology so interesting (and effective) is that there is no digital key stored in the IC’s memory. Rather, ChipDNA makes use of the random variations that are inevitable in the fabrication of semiconductor circuits, somehow converting these variations into a digital key that is unique to each device.
Thus, the key is “stored” in the analog characteristics of each individual IC, and this method means that the key is generated by means of a “physically unclonable function” (PUF), as shown in the shaded portion of the following block diagram.
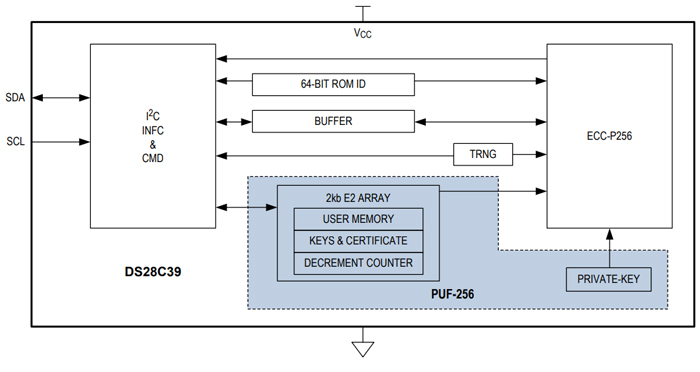
Block diagram of DS28C39, including a PUF. Image used courtesy of Maxim Integrated
Nicely done, Maxim! You figured out a way to turn the problem of semiconductor parameter variation into a robust security solution.
Related Articles
What do you think is the most critical security challenge currently facing electrical engineers? What authentication parts have you used in previous designs? Leave a comment and let us know.